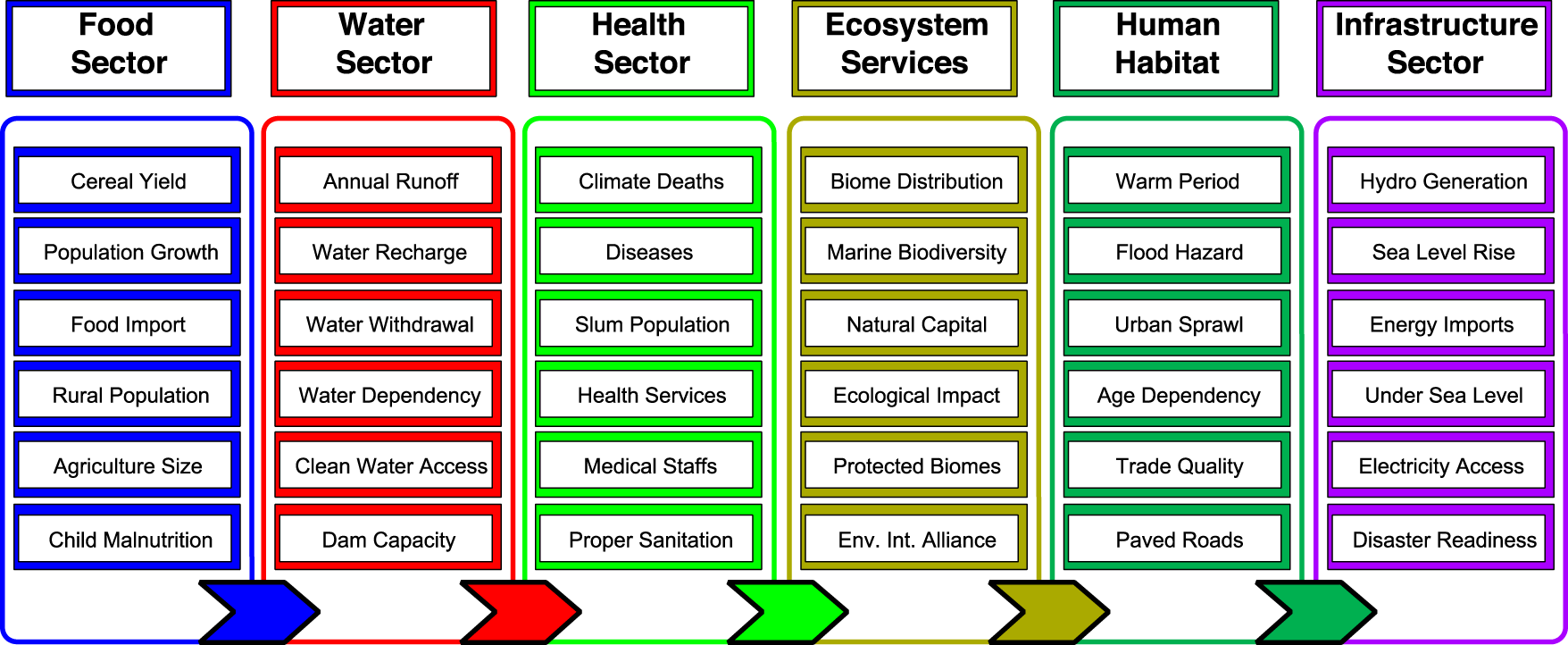
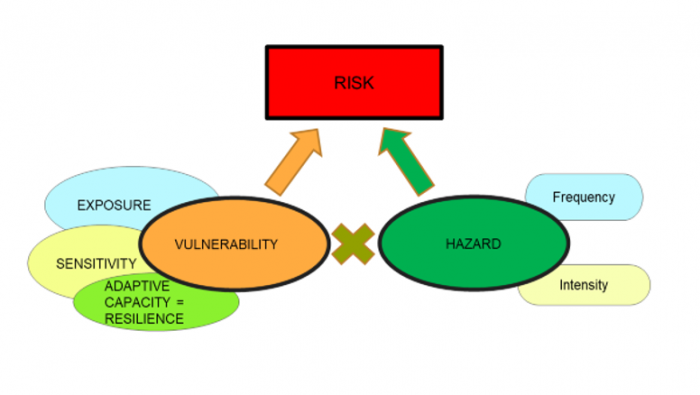
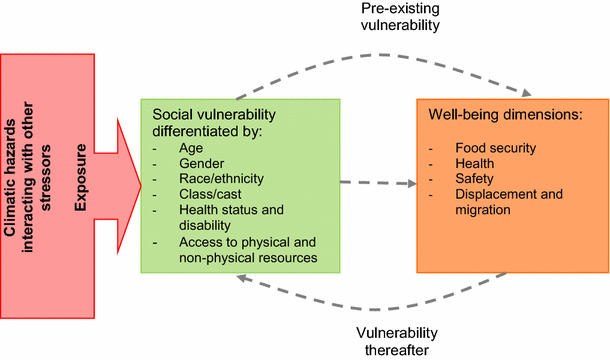
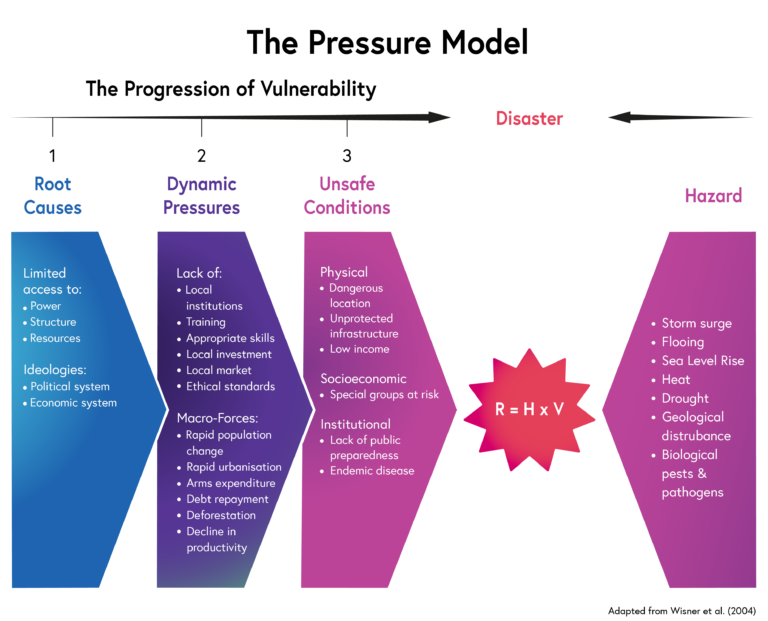
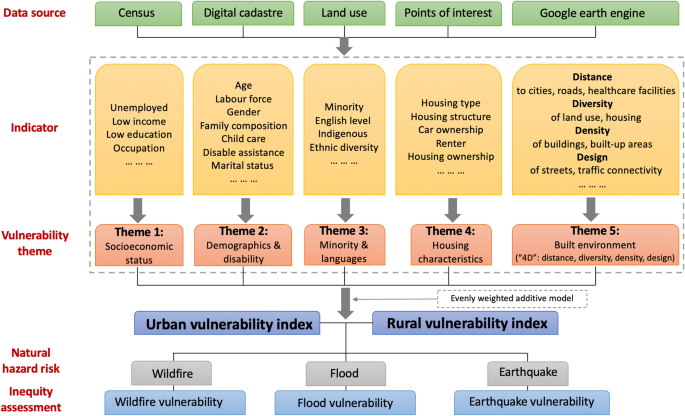
The four key drivers of vulnerability and the types of characteristics... | Download Scientific Diagram

Frontiers | Poverty Vulnerability and Health Risk Action Path of Families of Rural Elderly With Chronic Diseases: Empirical Analysis of 1,852 Families in Central and Western China